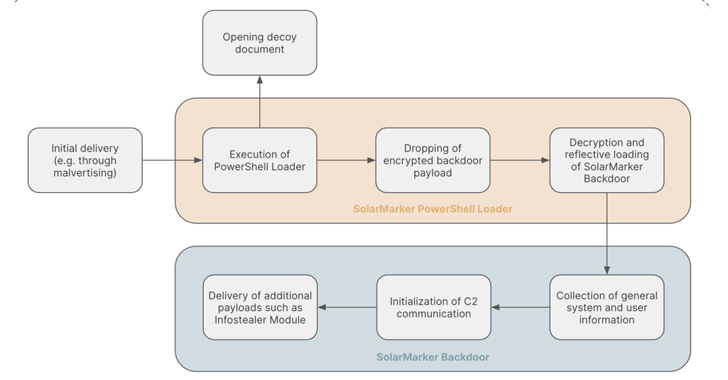
From Security Week – AI Companies Make Fresh Safety Promise at Seoul Summit, Nations Agree to Align Work on Risks
[[{“value”:”Leading artificial intelligence companies made pledge to develop AI safely, while world leaders agreed to build a network of publicly backed safety institutes to advance research and testing of…

.webp)








_Skorzewiak_Alamy.jpg)